Was definiert eine Identity? Eine Identity wird durch eine ein-eindeutige Zuweisung an eine Person, Gruppe oder einen Prozeß dargestellt. Diese Identity ist Grundlage für Authentifizierung und Autorisierung. Die Ein-Eindeutigkeit der Identity muß gewährleistet sein. Wann wird eine Identity benutzt? Eine Identity kommt immer dann zum Tragen, wenn auf ein rollenbasiertes System zugegriffen wird. Wann gilt eine Identity als kompromittiert? Eine Identity wird als unsicher/kompromittiert gekennzeichnet, sobald diese mit Authentifizierungsdaten zur Verfügung steht. Dabei ist es…
Opitz Consulting lebt und verbreitet den DevOps Gedanken und schult seine Mitarbeiter mit einem Fast Track Schulungsprogramm. Dieses besteht aus…
The issue ist reported newly as a Bug from Oracle… Technology, KeyWords: WebLogic Server 12.1.3.0.0., 10.3, Exception; java.net.ProtocolException Error Message:…
The OFM Summer Camps 2015 is finished successful (August 17th „“ 21st 2015 Lisbon Portugal) and Oracle Fusion Middleware community…
Es gab am 20. Juni in Nürnberg den DOAG 2014 Konferenz. Mein Kollege Frank Burkhardt und ich haben dort einen…
Key words: IT-Security, WebLogic Server, Authorization, authorization process, Role Mapping, Roles and XACML Role Mapping Provider Let“™s continue with Authorization…
Key words: IT-Security, WebLogic Server, WebLogic Security Framework, Authorization, authorization process, Role Mapping, Roles, Adjudication Process, Security Service Provider Interfaces…
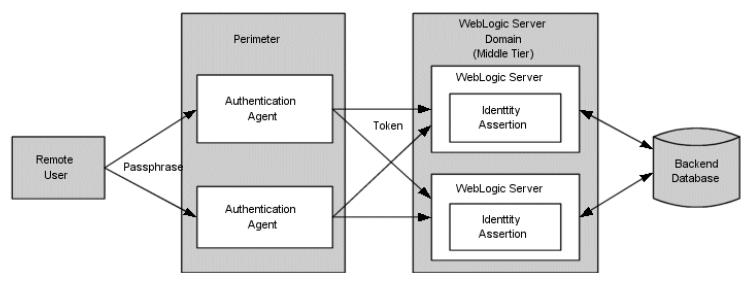
Key words:IT-Security, Security Challenges, OPSS Architecture, WebLogic Server, JAAS, JAAS LoginModules, Authentication, Basic Authentication, Certificate Authentication, Digest Authentication, perimeter Authentication…
I tried to discuss about „perimeter authentication“ in one extra part of IT-Security“™s blogs, because this authentication“™s process is an…