Key words: IT-Security, WebLogic Server, Authorization, authorization process, Role Mapping, Roles and XACML Role Mapping Provider
Let“™s continue with Authorization topic. We discussed about the Authorization Process and its main components such as WebLogic Security Framework and Security Provider. Now, we look at Security Provider“™s subcomponents: Role Mapping and Security Policies.
The Role Mapping: Is access allowed?
Role Mapping providers help to clear, weather a user has the adequate role to access a resource? The Authorization provider can with this role information answer the „is access allowed?“ question for WebLogic resources.[1]
The Role Mapping Process
Role mapping is the process whereby principals are dynamically mapped to security roles at runtime. The WebLogic Security Framework sends Request Parameter to specific Role Mapping provider that is configured for a security realm as a part of an authorization decision. Figure 1 Role Mapping Process presents how the Role Mapping providers interact with the WebLogic Security Framework to create dynamic role associations. The result is a set of roles that apply to the principals stored in a subject at a given moment.[2]
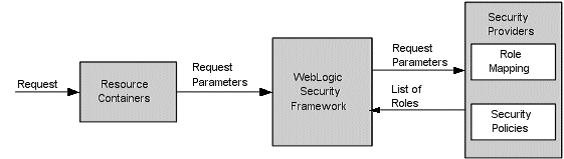
Figure 1 Role Mapping Process
Let“™s review each part again[3]:
- The request parameters are including information such as the subject of the request and the WebLogic resource being requested.
- Role Mapping provider contains a list of the roles. For instance, if a security policy specifies that the requestor is permitted to a particular role, the role is added to the list of roles that are applicable to the subject.
- As response, get WebLogic Security Framework the list of roles.
- These roles can then be used to make authorization decisions for protected WebLogic resources, as well as for resource container and application code. I“™m going to discuss about that in part 9.
Configuring a Role Mapping Provider
The XACML Role Mapping provider and DefaultRoleMapper are included by WebLogic Server. In addition, you can use a custom Role Mapping provider in your security realm too. By default, most configuration options for the XACML Role Mapping provider are already defined. However, you can set Role Mapping Deployment Enabled, which specifies whether or not this Role Mapping provider imports information from deployment descriptors for Web applications and EJBs into the security realm. This setting is enabled by default. In order to support Role Mapping Deployment Enabled, a Role Mapping provider must implement the DeployableRoleProvider SSPI. Roles are stored by the XACML Role Mapping provider in the embedded LDAP server.[4] XACML Role Mapping provider is the standard Role Mapping provider for the WebLogic Security Framework. To configure a Role Mapping provider:
- In the Change Center of the Administration Console, click Lock & Edit
Figure 2 Change Center
- In the left pane, select Security Realms and click the name of the realm you are configuring.
Figure 3 Domain Structure: Click Security Realms
Figure 4 Summary of Security Realms
- Select Providers > Role Mapping. The Role Mapping Providers table lists the Role Mapping providers configured in this security realm
Figure 5 myrealm: Role Mapping
- Click New. The Create a New Role Mapping Provider page appears.
Figure 6 WebLogic Server default Role Mapping Provider: XACMLRoleMapper
- In the Name field, enter a name for the Role Mapping provider. From the Type drop-down list, select the type of the Role Mapping provider (e.g. DefaultRoleMapper or XACMLRoleMapper) and click OK.
Figure 7 a New Role Mapping Provider: Default_1
- Select Providers > Role Mapping and click the name of the new Role Mapping provider to complete its configuration.
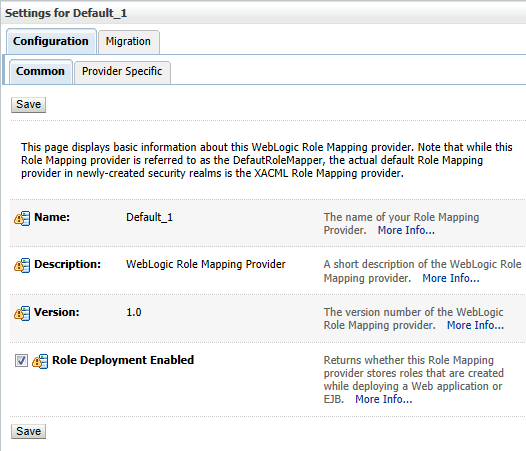
Figure 8 Role Mapping Configuration
- Optionally, under Configuration > Provider Specific, set Role Deployment Enabled if you want to store security roles that are created when you deploy a Web application or an Enterprise JavaBean (EJB) (See Figure 8 Role Mapping Configuration).
- Click Save to save your changes.
- In the Change Center, click Activate Changes and then restart WebLogic Server.
XACML Role Mapping Provider
As we discussed above, a WebLogic security realm is configured by default with the XACML Role Mapping provider. It implements XACML 2.0, the standard access control policy markup language (the eXtensible Access Control Markup Language). WebLogic XACML Role Mapping Provider is saved as a .dat file und available on e.g.: $Domain-Home/XACMLRoleMapper.dat and has the following options (see Figure 8 Role Mapping Configuration):
- Name: The name of your WebLogic XACML Role Mapping Provider.
- Description: The description of your Weblogic XACML Role Mapping Provider.
- Version: The version of your Weblogic XACML Role Mapping Provider.
- Role Deployment Enabled: Returns whether this Role Mapping provider stores roles that are created while deploying a Web application or EJB.
You can see file structure on the following example: XACMLRoleMapper.dat has different User/Groups. For each User assigned particular Roles, Policies and associated resources. For example, you see description of Group and User „Administrators“ below:
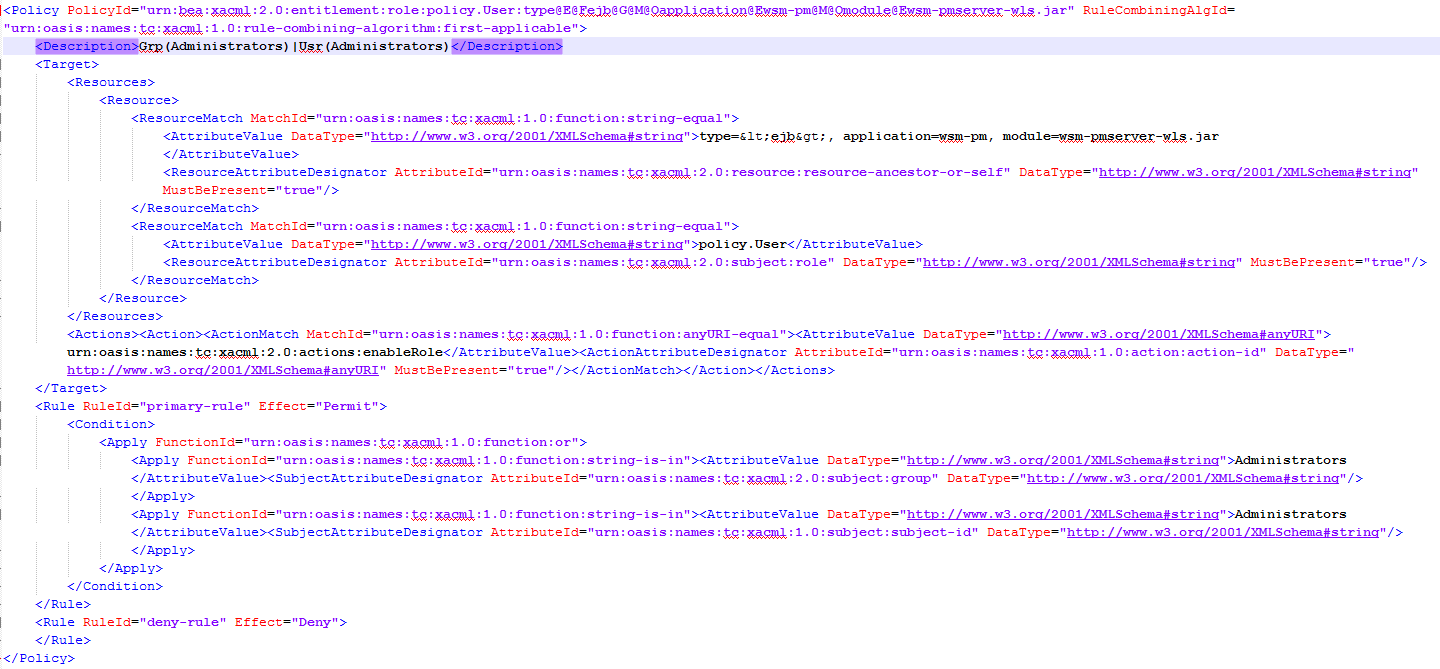
Figure 9 XACMLRoleMapper.dat: description of Group and User „Administrators“
You see a policy contains Description, Target and Rule. Each element is associated to different attributes and with this form prepared one „authorization matrix“ that it helps to decide Application Server about a user or a group. Continued“¦
References
See too last parts of IT-Security and Oracle Fusion Middleware:
- https://thecattlecrew.net/2014/02/17/it-security-weblogic-server_1/
- https://thecattlecrew.net/2014/03/05/it-security-part-2-weblogic-server-and-oracle-platform-security-services-opss-2/
- https://thecattlecrew.net/2014/03/14/it-security-part-3-weblogic-server-and-java-security-features/
- https://thecattlecrew.net/2014/06/05/it-security-weblogic-server-and-authentication-part-4/
- https://thecattlecrew.net/2014/06/22/it-security-part-5-weblogic-server-perimeter-authentication-and-identity-assertion/
- https://thecattlecrew.net/2014/07/23/it-security-part-6-weblogic-server-and-authorization/
[1] Oracle® Fusion Middleware Securing Oracle WebLogic Server 11g Release 1 (10.3.6), E13707-06
[2] Oracle® Fusion Middleware Understanding Security for Oracle WebLogic Server 11g Release 1 (10.3.6), E13710-06
[3] Oracle® Fusion Middleware Understanding Security for Oracle WebLogic Server 11g Release 1 (10.3.6), E13710-06
[4] Oracle® Fusion Middleware Securing Oracle WebLogic Server 11g Release 1 (10.3.6), E13707-06




2 Kommentare
Pingback: IT-Security (Part 7): WebLogic Server, Roles, Role Mapping and Configuring a Role Mapping Provider by Mohammad Esad-Djou | ora fusion community
Pingback: IT-Security (Part 7): WebLogic Server, Roles, Role Mapping and Configuring a Role Mapping Provider – Mohammad Esad-Djou