Most bigger companies are today building up a enterprise SOA. On of the key characteristic of the enterprise SOA is the machine to machine communication.
The communication between the machines has to be secured. Important is
1.) to keep the the content of the sent messages private
2.) ensure only the authorized machine can invoke operations
The first point can be achieved using HTTPS communication for webservice calls.
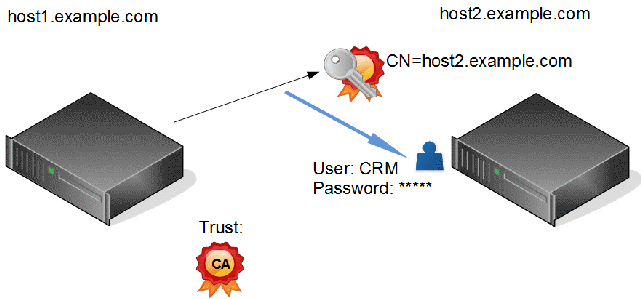
Username and Password over HTTPS
The second point is at user to machine communication often realized using a username and a password combination and can also be used for machine to machine communication.
On the client side (host1) the certificate of the certificate authority is needed to establish a trust to the CA.
On the host side there is the host certificate of machine host2 with the associated private key. This certificate is used to make sure machine host1 is really talking to machine host2. The attribute CN inside the certificate must match to the full qualified hostname of machine host2.
The username and password is transmitted over the encrypted HTTPS communication. The host verifiers user and password and has an association to the account used for the operation and the rights the caller has.
Most IT professionals know this type of communication and authentication. But there is an other well supported option: client certificates.
Client certificates
In this blog post I will describe the basics how a m2m communication with client certificates work.
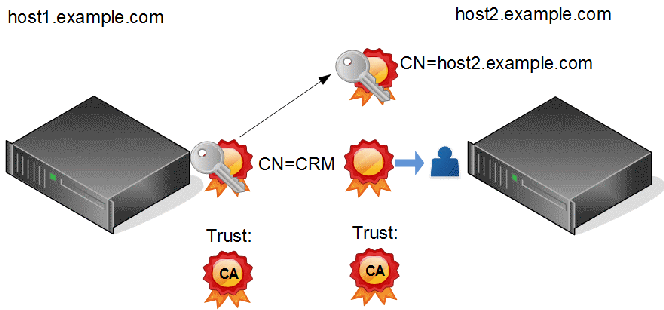
In this picture is the call of a webservice using HTTPS and client certificate described:
On the client side (host1) the client certificate of the system e.g. CRM with the associated private key is needed. This certificate is used to identify the (logical) system to the machine host2. If the system is a cluster the certificate is the same for all machines.
On the host side there is the host certificate of machine host2 with the associated private key. This certificate is used to make sure machine host1 is really talking to machine host2. The attribute CN inside the certificate must match to the full qualified hostname of machine host2.
Additionally we need the client certificate of the system (e.g CRM) without the private key on machine host2. Inside machine host2 there is a association from the client certificate of the system CRM to an account used for the operation and the rights the caller has. How this association is created depends on the application software on machine host2.
On both sides we need the certificate of our CA. This certificate is need to verify, that all other certificates are issued by the trusted CA and not by a third party. Inside the enterprise it is a best practice to trust on the predefined list of trusted CAs and not on the list automatically provided by Java, SAP or an other manufacturer. Instead a custom list containing only the own trusted CA should be used.
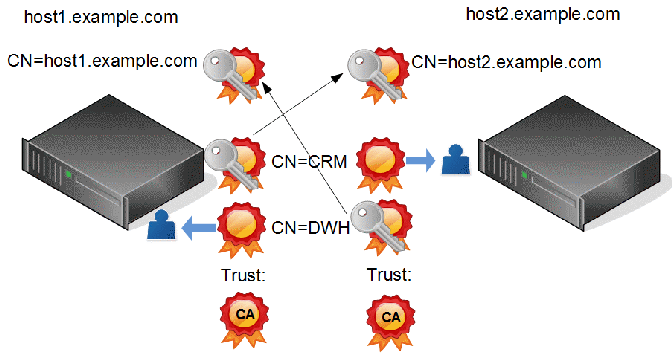
Bidirectional communication with client certificates
If the communication can be initiated from both machines or we are using asynchronous webservices we need to double the number of certificates:
On both machines we have a (different) client certificate identifying the system with the associated private key for proofing the identity of the machine.
On both machines we have a (different) host certificate with the associated private key matching the full qualified hostname of the machine. Additionally the client certificate of the other system is need for the association with the account used for processing the requests.
Security considerations
– Keep the private key of the client certificate secured. If someone has this private key he can easily do everything the machine is able to do.
– Don“™t use wildcard certificates for host certificates because a wildcard certificate can act as every machine of the enterprise and there for with e.g. spoofing of the DNS listen to any communication.
Bernhard Mähr @ OPITZ-CONSULTING published at https://thecattlecrew.net/




2 Kommentare
Pingback: Setting up a own CA for the enterprise | The Cattle Crew Blog
Pingback: Setting up a own CA for the enterprise - Stumbling Blo(g|ck)