For connecting to Oracle Human Workflow Engine via the provided client API, username and password of an admin user are needed. These credentials could also be useful during task processing, when actions on a task has to be performed on behalf of a user, for example in case of holidays or illness. But how can to manage the admin users credentials in secure way, independent from the target environment?
A first approach is to use a mechanism where the credentials were provided as context parameters in the web.xml, of a Facade Web Service in front of the client API to hide complexity and to force upgrade protection in case of API changes. When deploying this Web Service facade, the parameters are replaced using a deployment plan. This solution works, but has the disadvantage that username and password of the admin user are contained in the deployment plan as clear text. From a SysOps perspective this mechanism is not appropriate.
So another possibility must be found to manage user credentials in a consistent and secure way. An approach to ensure the secure management of credentials is to use the Oracle Credential Store Framework (CSF), provided by Oracle Platform Security Services (OPSS). Configuring and using CSF is quite simple and done in a few steps:
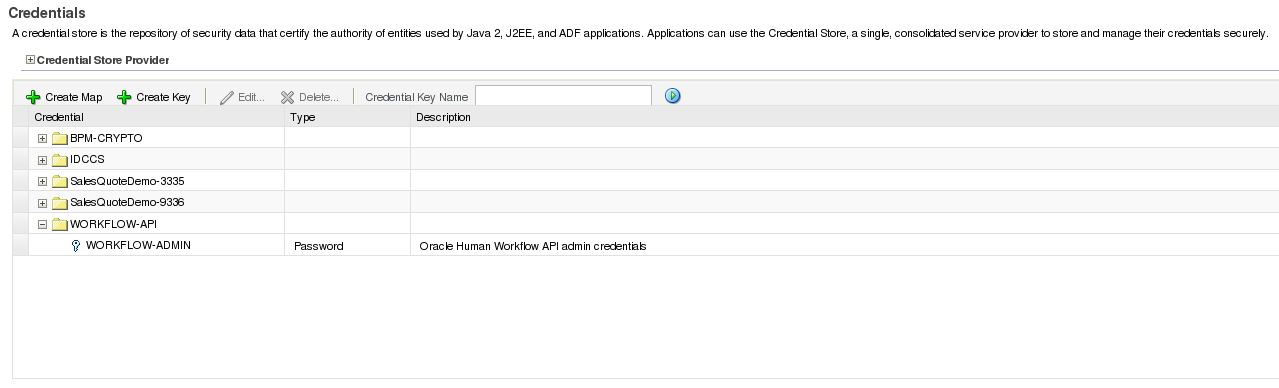
1. Create Credentials Store in EM (Right click on Weblogic domain > [Domainname] and then choose Security > Credentials from the Dropdown menu)
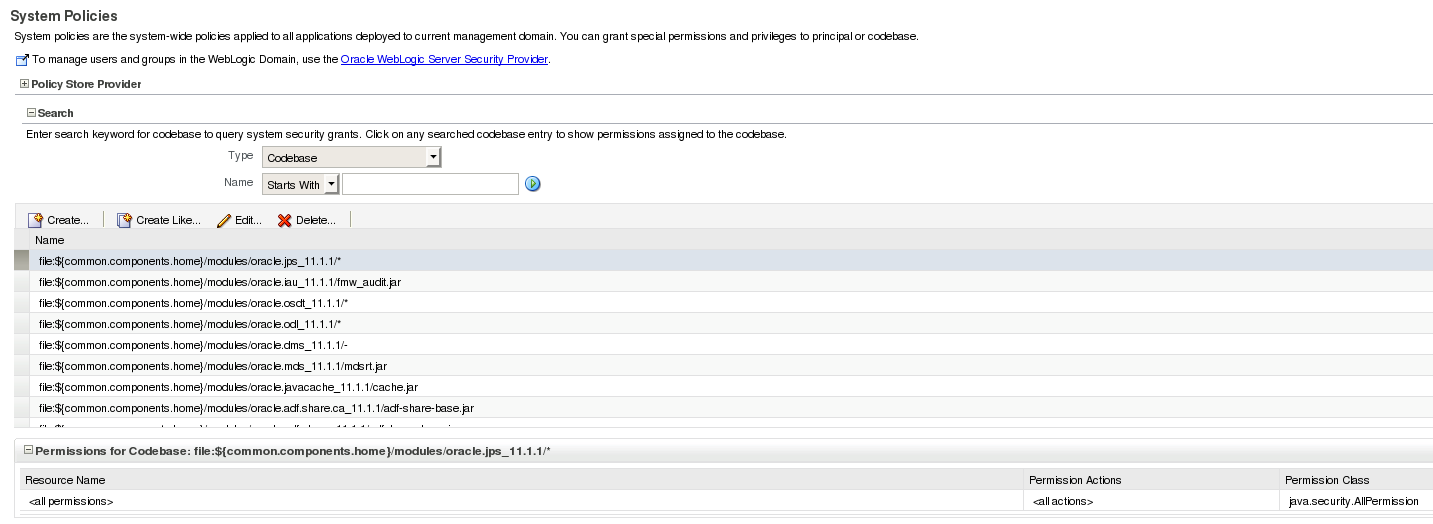
2. Configure System Policy to authorize access to the configured Credential Store (Right click on Weblogic domain > [Domainname] and then choose Security > Credentials from the Dropdown menu)
The configurations, needed to allow read-only access from an application, contains the following information
[code language=“text“]
Type: Codebase
Codebase: file:${domain.home}/servers/${weblogic.Name}/tmp/_WL_user/
Permission:
Permission Class: oracle.security.jps.service.credstore.CredentialAccessPermission
Resource Name: context=SYSTEM,mapName=WORKLIST-API,keyName=*
Permission Actions: read
[/code]
3. Deploy the application
Managing the credentials in the Credential Store may also be done by using WLST functionalities, which would be more maintainable from a SysOps perspective. Details on that could be found here. The system policies may be directly edited in
Accessing the so configured Credential Store by a server application is done by using the lines of code below. For developing the shown CSF access, jps-api.jar must be in the classpath of the application. At runtime the needed dependencies are provided by Oracle Weblogic Server.
[code language=“java“]
package com.opitzconsulting.bpm.connection;
import java.security.AccessController;
import java.security.PrivilegedActionException;
import java.security.PrivilegedExceptionAction;
import oracle.security.jps.service.JpsServiceLocator;
import oracle.security.jps.service.credstore.CredentialStore;
import oracle.security.jps.service.credstore.PasswordCredential;
public final class CsfAccessor {
static PasswordCredential readCredentialsfromCsf(String pCsfMapName, String pCsfKey) {
try {
return AccessController.doPrivileged(new PrivilegedExceptionAction
@Override
public PasswordCredential run() throws Exception {
final CredentialStore credentialStore = JpsServiceLocator.getServiceLocator().lookup(CredentialStore.class)
return (PasswordCredential) credentialStore.getCredential(pMapName, pKey);
}
});
} catch (Exception e) {
throw new RuntimeException(String.format(„Error while retrieving information from credential store for Map [%s] and Key [%s]“, pCsfMapName, pCsfKey), e);
}
}
}
[/code]
When having more applications that need to access credentials from the Credentials Store, it is recommended to implement the access to CSF centrally and provide the functionality as a shared library within Weblogic Server. Otherwise you have to configure the corresponding System Policies, which authorizes the access to CSF, separate for every new application that needs to have access to CSF. Using the shared library approach, only the shared library itself has to be authorized for accessing the Credentials Store. Applications that need to access CSF must only specify the dependency to the shared library in the application’s deployment descriptor file, like weblogic-application.xml.
[code language=“xml“]
[/code]
In order to encapsulate the access to CSF and to avoid the publication of the PasswordCredential object instance, we decided to further encapsulate the CSF access by a special Connection object, which establishes the connection to the Human Workflow API and can provide a WorkflowContext for the corresponding admin user.
[code language=“java“]
package com.opitzconsulting.bpm.connection;
import java.util.Map;
import oracle.bpel.services.workflow.client.IWorkflowServiceClient;
import oracle.bpel.services.workflow.client.IWorkflowServiceClientConstants.CONNECTION_PROPERTY;
import oracle.bpel.services.workflow.verification.IWorkflowContext;
import oracle.bpm.client.BPMServiceClientFactory;
import oracle.security.jps.service.credstore.PasswordCredential;
public class HumanWorkflowApiConnection {
private IWorkflowServiceClient workflowServiceClient;
public HumanWorkflowApiConnection(Map
final BPMServiceClientFactory bpmServiceClientFactory = BPMServiceClientFactory.getInstance(pProperties, null, null);
workflowServiceClient = bpmServiceClientFactory.getWorkflowServiceClient();
}
public IWorkflowServiceClient getWorkflowServiceClient() {
return workflowServiceClient;
}
public IWorkflowContext createWorkflowContextForAdmin(String pCsfMapname, String pCsfKey) {
final PasswordCredential passwordCredential = CsfAccessor.readCredentialsfromCsf(pCsfMapname, pCsfKey);
try {
return workflowServiceClient.getTaskQueryService().authenticate(passwordCredential.getName(),
passwordCredential.getPassword(), „jazn.com“);
} catch (Exception e) {
throw new RuntimeException(String.format(„Exception while authenticating Admin User [%s]“, passwordCredential.getName()), e);
}
}
}
[/code]
Links:



1 Kommentar
Pingback: Using Credential Store Framework when communicating with Oracle Human Workflow API by Sven Bernhardt | SOA Community Blog